Self Notes: Web Security Academy Directory Traversal Lab 6

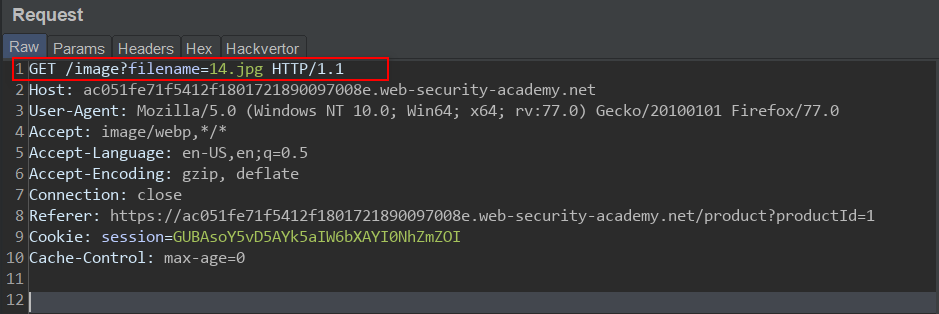
Link to Lab 6 To solve this lab, we need to bypass the application's check for file type extension and exploit the directory traversal vulnerability in the image display endpoint. Check whether the application filters our input: Response from Server: The server doesn't recognize the file, let's try bypassing with null byte: Response from Server: Lab Solved!