Self Notes: Web Security Academy HTTP Request Smuggling Lab 8
Link to Lab 8
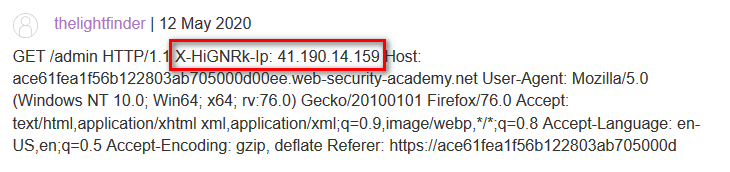
After the smuggled request has been executed the comment is posted which contains the header 'X-HiGNRK-Ip'. All that is left now is to smuggle a request with this header. Easy:
Lab 8 is a bit different from the previous Lab, the Front-end server doesn't support chunked encoding the Back-end server does, CL-TE, the task is to find out the HTTP Request headers added by the Front-end server, when forwarding the request to the Back-end server and then as usual delete the user Carlos. The admin panel is not protected in this level as the previous one so we have direct access:
Response from the server:
So, we just have to worry about the Headers. The headers will be smuggled through the comment section using this request:
The Back-end server will only process the first chunk leaving the rest as smuggled request, the next request will then be appended to the smuggled request and used to post the comment. Hence, the large Content-Length.
The response from the server after executing the smuggled request:
Time to delete Carlos:
Once the smuggled request is executed:
Lab Solved.










Comments
Post a Comment