OverTheWire: Bandit Lab
Bismillahirrahmanirrahim (In the name of Allah the most gracious, the most merciful)
So recently I and @electro decided to solve wargames and CTFs in the spirit of honing the skills and because we are preparing for something really important (another post for another day). We decided to start with the labs at overthewire and the first on the list was Bandit Lab. Bandit Lab was a fun experience, mostly easy, except for one or two tricky levels, level 26 and level 33 in particular. This Labs weren't so difficult but required a bit of thinking outside the box, hence why am documenting them.
NB: this writeup doesn't include our thought process while solving the levels
Level 26
Level Description
When we attempt to login to this level using the private key obtained from the previous level we get automatically logged out and since the level goal already informed us that we are dealing with a different shell, we need to figure out what it is and how to break out of it.
Above is the banner that gets printed out when we attempt to log in and we get automatically logged out. So how do we figure out the shell we are dealing with? well, we will have to look at the /etc/passwd file from the previous level, since it holds the login information of all users on the system.
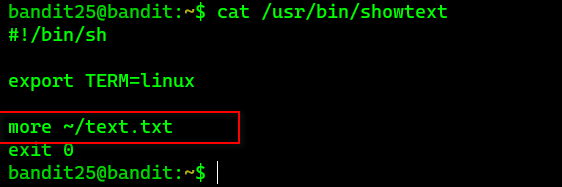
And indeed the shell isn't bash but some unknown shell showtext, let's check out what it is.
It turned out showtext is just a short shell script that uses more utility to show the content of the text.txt file and then exit. Now, this is the tricky part, since the level goal already recommended reading man pages for more which we did we figured out we could run shell commands with more utility.
The problem was that shell kept exiting before we even had the chance to interact with more. After a lot of headbanging and reading of the manual pages for ssh, vi, and more it turned out we just needed to resize the terminal window and we will be able to intercept the shell script in more before it exits.
Login in successful and we are now in more so shell script hasn't exited. Running command directly via more didn't turn out to work successfully so we figured from the documentation that we could start the vi editor from more with the v command.
The reason the command didn't work directly in more was that we were still using the showtext shell and we can see that by attempting to view the current shell from vi.
Level 33
Level Description
It's another shell escape level. I must confess without the amazing team effort with @electro am not sure I would have figured this out quickly. So upon login to level32, the shell has been set to change all commands to uppercase.
When we check the /etc/passwd file we confirm that the shell is indeed not bash.
The shell is uppershell and is not even readable. Our approach to defeating this level relied on shell expansion (will be discussed fully in another post) and the fact that /tmp/ dir is globally writable.
In summary, what we did was create a directory under /tmp/ with our custom shell script which we made executable by anyone and then relied on shell expansion to do the heavy lifting for us. I plan to create another post to explain the above concept in detail since it's late now (about 01:48 AM) and I need to wake up early tomorrow.
So that's basically it on the two levels that we found to be really interesting in the bandit lab, watch out for natas and krypton labs coming soon inshaAllah.


















i love it, it's a little bit challenging, i'm coming for it too
ReplyDelete