Self Notes: Web Security Academy File upload vulnerabilities Lab 3
(In the name of Allah, the most gracious, the most merciful) بِسْمِ اللَّهِ الرَّحْمَنِ الرَّحِيم
It's been a while I wrote, mostly due to work and a little bit of laziness. Anyways I recently came across a lab from PortSwigger web security academy that I spent so much time without solving (I was really disappointed with myself when I figured out the solution), so as usual I am writing about it so I don't forget and so it may serve as a reference in the future.
The Lab is under the file upload vulnerabilities section, it is tagged as practitioner level difficulty (hence, my disappointment).
Task: This lab contains a vulnerable image upload function. The server is configured to prevent the execution of user-supplied files, but this restriction can be bypassed by exploiting a secondary vulnerability.
To solve the lab, upload a basic PHP web shell and use it to exfiltrate the contents of the file /home/Carlos/secret. Submit this secret using the button provided in the lab banner.
You can log in to your own account using the following credentials: wiener:peter
So the task is to exploit a vulnerable PHP upload functionality and upload a web shell, also it's stated that the server is configured not to execute the user-supplied files. Let's investigate if that's true. We are provided the following file upload form:
But of course, what really matters is the request and response we get from the server, so we upload the following shell:
Our script is not executed but rendered as plain text so we can confirm that scripts files in this directory are not executable, we will need to find a bypass. But from the task, we've already been given a tip that we will need to exploit a secondary vulnerability; path traversal 😃 (something we've dealt with previously), so I begin to search for any exploitable path traversal vulnerability but to no avail, I even when on to use Burp Intruder payload for path traversal fuzzing, but that also yielded nothing. It turned out the problem was from me, I have already made an assumption about the vulnerability, that it would be in another functionality as it's typical of PortSwigger labs, but unfortunately, I was wrong. Of course, I only figured that out after wasting so much time. My first breakthrough came from this observation:
Whenever I added a path traversal sequence to any resource endpoint as above we get a 404 response, this behavior was consistent for all endpoints except (you guessed it 😃):
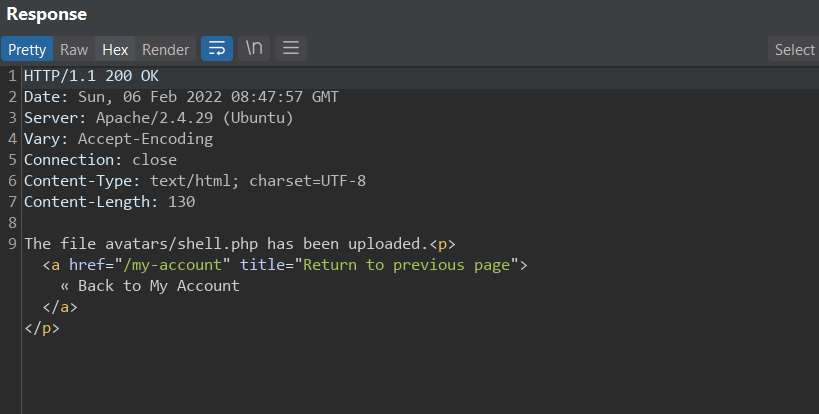
And we get a response that the file was uploaded successfully to our specified directory, notice also that the filename is completely URL-encoded, this is because it won't work when you pass it as plaintext, probably because there is a reverse proxy normalizing the path or something else, not sure, but whenever in doubt URL-encode the input. Let's try executing our PHP shell now.
Lo and behold, our script gets executed and we have a shell. All that is left is to retrieve Carlos' secret file. Note that our shell takes in a base64 encoded input and decodes it before executing it as a system command.













Comments
Post a Comment