Self Notes: Web Security Academy HTTP Request Smuggling Lab 3
Lab 3 can be found here.
For this Lab, a Front-end and Back-end servers that handle duplicate HTTP Request headers differently are provided, the task is to find a way to obfuscate the Transfer-Encoding Header to achieve HTTP request smuggling. The provided endpoint accepts POST request for posting comments as follows:
Since both servers accept Transfer-Encoding header the above request chunk encoded becomes:
Sending the request to the server, the response was:
a confirmation redirect is obtained, meaning the server is happy with us, so far so good. Since the essence of the Lab is to play with how the server handles duplicate headers, we attempt this:
the server still isn't complaining:
well, that's because at this point both the Content-Length (CL) and Transfer-Encoding (TE) Header values are valid, therefore even if one is using the CL and the other is using the TE we don't notice any discrepancy. Let's assume that the Front-end Server processes the first Header and the Back-end processes the second, this will mean that the Front-end uses the Content-Length, since Transfer-Encoding: x isn't valid, while the Back-end uses Transfer-Encoding since the Header is valid and if this hypothesis is correct, then we have successfully induced a CL-TE smuggling vulnerability for a TE-TE Front-end Back-end server pair, to test our hypothesis let borrow a payload from the HTTP Request Smuggling Captain, James Kettle, his blog post contains everything you need to get started with Request Smuggling. Modified Request with payload below:
If our CL-TE hypothesis is correct, then sending the request for the first time will cause the Back-end socket to be poisoned this is because of the 'G' appended to the end of the request body since the Back-end server will stop processing the request when it encounters the '0' character, leaving 'G' for the next request. The server's response was:
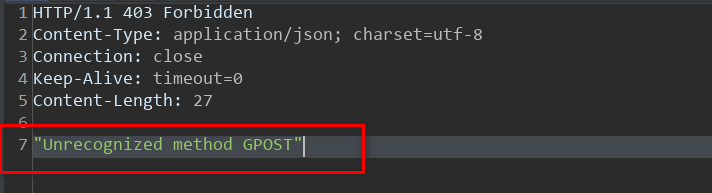
which makes sense, since it has completely ignored the 'G' at the end of the request body, but what happens when we send the same request again? this:
well, this proves our hypothesis and solves Lab 3, the 'G' got appended to start of the next request leading to an unrecognized method 'GPOST'. We have successfully desynchronized the Back-end Front-End server pair and smuggled the unauthorized request method. The intended or provided solution for this Lab on Web Security Academy is:
Reference











Comments
Post a Comment