Self Notes: Web Security Academy HTTP Request Smuggling Lab 4
Lab 4 can be found here.
For Lab 4 our task is to confirm CL-TE Vulnerability via differential Response. A Front-end Back-end server pair has been provided, the Front-end server does not support chunked encoding, to solve the Lab we need to smuggle a request to the Back-end server so that subsequent request to the web-root (/) results in a 404 Not Found response. Like Lab 3 the provided endpoint is a comment posting section as below:
Response is:
We got a confirmation redirect. From the lab task, we have already been informed that the Front-end Back-end Server pair is CL-TE, meaning that the Front-end support Content-Length Header only while the Back-end support Transfer-Encoding Header, therefore avoiding the need for any test, we use the following request:
The above request now includes Transfer-Encoding: chunked so that the Back-end server will read a chunked request, the request also includes an extra payload which will be ignored by the Back-end server and will poison the next request, sending the above request result in normal response:
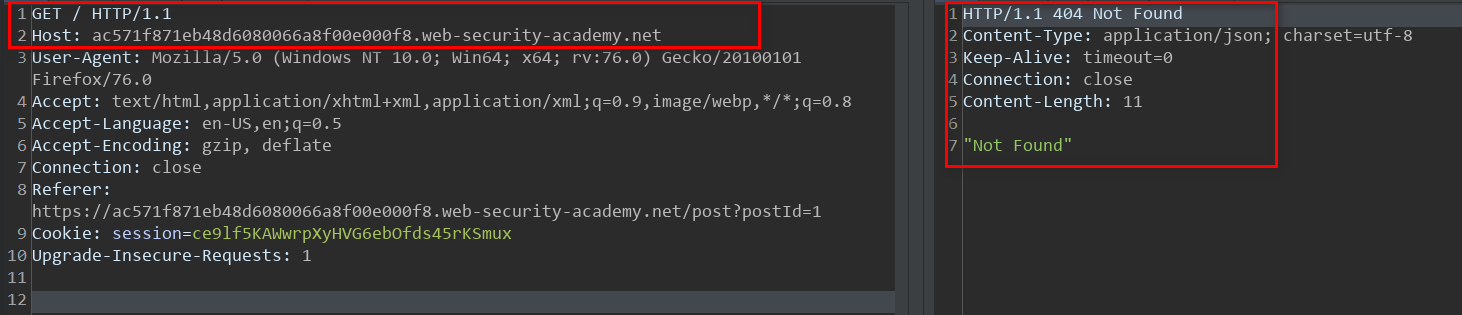
As expected a normal response is obtained from the server although the Back-end socket has now been poisoned with our payload. Any request to the server will now result in 404 not found response as below:
A valid request to the already poisoned Back-end server yielded a 404 Not Found response. Lab 4 solved.







Comments
Post a Comment